Tor Browser
Browse anonymously and protect your privacy online with military-grade encryption
Download Now
Free for Windows, Linux, macOS. No registration required.
One of over 130 tools we've selected. No paid listings.
How we review software →About Tor Browser
Tor Browser is a powerful, free web browser designed to protect your online privacy and anonymity. Built on the foundation of Mozilla Firefox, it routes your internet traffic through the Tor network—a vast network of volunteer-operated servers distributed worldwide. This unique approach makes it nearly impossible for anyone to track your browsing activity, physical location, or identify you based on your internet usage.
What Makes Tor Browser Special
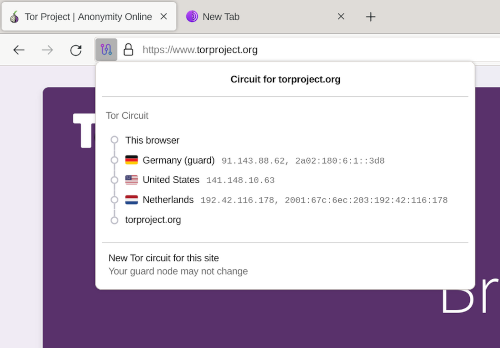
The browser automatically encrypts your data multiple times before sending it through three random relay servers (called nodes) in the Tor network. Each relay only knows the location of the previous and next relay, never the complete path. This "onion routing" technique ensures that no single point in the network can link your traffic back to you. When your data finally reaches its destination, it's decrypted at the exit node, making your browsing appear to originate from that node's location rather than your actual location.
Privacy by Design
Every aspect of Tor Browser is engineered to defend against surveillance and fingerprinting. The browser automatically clears your cookies and browsing history after each session, and it's configured to prevent websites from accessing information that could identify you. This includes blocking third-party trackers, defending against browser fingerprinting techniques, and isolating each website you visit so they can't track you across sessions.
Access Without Restrictions
Tor Browser enables access to websites and services that might be blocked in your country or network. Whether you're a journalist working in a restrictive environment, an activist coordinating with others, or simply someone who values privacy, Tor provides the tools to communicate and access information freely. The browser also allows access to .onion sites—special websites only accessible through the Tor network that offer additional privacy protections.
Security Features
Beyond privacy, Tor Browser includes robust security features. It automatically upgrades connections to HTTPS when possible through HTTPS-Everywhere integration, blocks dangerous scripts by default with NoScript, and includes safeguards against malicious exit nodes. The browser receives regular security updates from the Tor Project team, ensuring protection against newly discovered vulnerabilities.
Who Uses Tor
Millions of people worldwide rely on Tor Browser daily. Law enforcement agencies use it for investigations, businesses protect their competitive intelligence, families safeguard children online, and individuals in oppressive regimes communicate safely. The Tor network processes billions of requests daily, demonstrating its critical role in preserving internet freedom globally.
Commitment to Open Source
Tor Browser is completely open source, meaning its code is publicly available for anyone to inspect, audit, and improve. This transparency ensures there are no hidden backdoors or vulnerabilities. A global community of security researchers, developers, and privacy advocates continuously works to enhance the browser's capabilities and maintain its security standards.
Key Features
Anonymous Browsing
Routes your traffic through the Tor network to hide your IP address and location from anyone conducting network surveillance or traffic analysis
Multi-Layer Encryption
Encrypts your data multiple times through three different relay nodes, making it virtually impossible to trace your activity back to you
No-Log Privacy Protection
Automatically clears cookies, browsing history, and cache after each session to prevent tracking and fingerprinting
Access to .onion Sites
Browse special .onion websites that are only accessible through the Tor network, providing extra security and privacy
Pros & Cons
Pros
- Strong anonymity and privacy protection through multi-layer encryption
- Free and open source with no hidden costs
- Bypasses censorship and geo-restrictions
- Cross-platform support (Windows, macOS, Linux, Android)
- Regular security updates from trusted developers
Cons
- Slower browsing speed due to traffic routing through multiple nodes
- Not suitable for streaming or downloading large files
- May be blocked by some websites and services
- Requires learning curve for optimal privacy settings